By: Simon Varley, Director of Digital Forensics
For a criminal defense attorney, understanding how law enforcement came to knock on their client’s door is extremely important. This can be a very tough thing to decern when presented with complex police reports and digital forensic analyses. Simon Varley, the Director of Digital Forensics with Purpose Legal, is here to streamline this process and make it easier to understand.
Simon calls the technique of understanding the case and understanding the digital evidence of the opposing side “The Chain of Suspicion”. The primary idea behind this is to visualize the steps made by the opposing side and what evidence they have or don’t have to connect to the defendant. By visualizing in this way, a defense attorney can identify weaknesses, assumptions, and even possible omissions in the opposing side’s presentation. This can allow the defense attorney to focus his time and effort on targeting certain aspects of the case that best serve his client’s interest.
What is the Chain of Suspicion?
The Chain of Suspicion involves the process of reviewing all the law enforcement forensic reports and discovery documents. That way, the attorney will be able to visualize how this process took place and narrow down anything that could be used as a way to counteract the opposite side and their presentation.
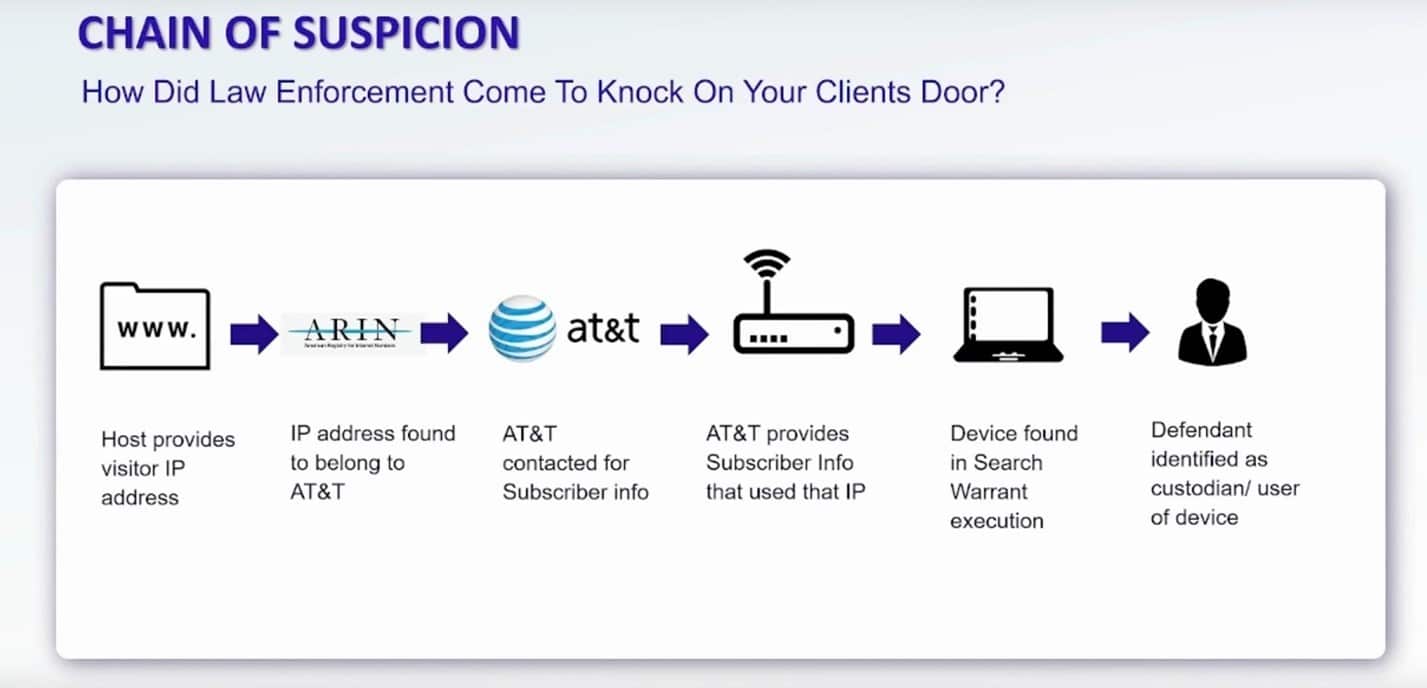
Example: let’s take as an example, a case involving insightful posts on a website. Law enforcement has charged an individual with these posts and provided materials to their attorney. In the discovery documents, we see that law enforcement started by contacting the hosting provider or owner of the website and requested for the poster’s IP address at the time of posting or the IP that was used to set up the account.
That IP address becomes an identifier which while not identifying the defendant directly points most likely to an internet provider. Normally an internet provider will have a block of IP addresses that it allocates when a subscriber goes online. The date and time of the use of the IP address is important also as addresses get reused and reallocated.
In this case law enforcement looked up the IP address and saw it belonged to AT&T. They then sent that IP address to ‘The AT&T Wireless (AW) National Subpoena and Court Order Compliance Center’ and provided the date and time. AT&T then returned the subscriber name and address that corresponded to the use of that IP. The subscriber was the Defendant in the case.
Is that the end of the process?
The subscriber’s name simply identifies the account used to access the internet and any person using any device connected to that subscriber’s WiFi would leave the same evidence. So it is important that law enforcement find the device used and then tie that to the suspect in the case to complete the ‘chain’.
In this example the evidence already collected was used to obtain a search warrant and law enforcement collected devices from the property of the Defendant. The laptop in this case was forensically imaged and analyzed and records of browser activity consistent with the insightful post were found.
There are many ways law enforcement can place a person infront of the computer at a specific time. One way is to determine if the login to the computer is password protected. During one case that Simon Varley worked on, a person was doing their taxes, 30 minutes prior to visiting a bad website. They logged into their H&R Block account, and it was very clear to the attorneys that based on the security measures and info provided the defendant was the one that accessed it.
In the above example the steps are quite clear and it’s a good way for the attorney to see what was done and why. In reality, there are more complex chains that can show weaknesses and gaps in the chain.
How can it be used to build a defense?
In the following example taken from an actual case worked by Simon, we work through a seemingly water-tight case that an attorney had struggled to find a way to approach.
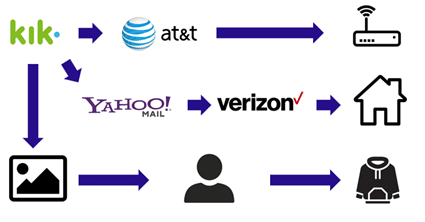
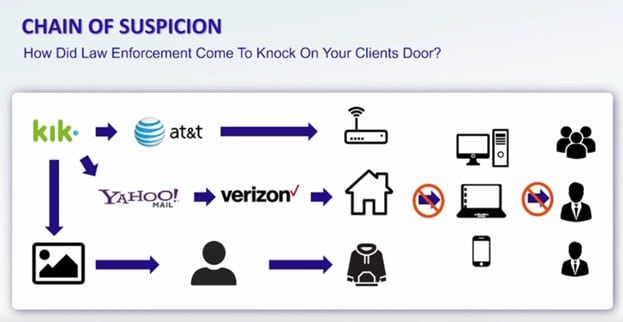
Example: The charges in the case were based on events that occurred on the chat application Kik. evidence against the defendant started with a chain based on an app named Kik. Law enforcement had the user profile of bad actor and requested from Kik all user information they had tied to the username in question.
Kik provided the IP address of the user and the email address used to register the account. The email was a Yahoo email so law enforcement contacted Yahoo and obtained the IP address that was last used to access the email account. The Kik IP address was registered to AT&T and the Yahoo IP was registered to Verizon.
Law enforcement sent the IP details to Verizon and AT&T and both responded with Mr and Mrs Defendant as the subscriber that had used those IP addresses. Additionally they had a video still captured from the Kik chat that looked like Mr Defendant wearing a dark hooded sweatshirt with three white letters on the front similar to one Mr Defendant owned.
This appeared to be a very strong argument put together by the opposing side and the defense attorney did not know where to begin with his defense.
Even though it seems water-tight we can see that actually there are two steps missing in their working through the case: the device, and the person. In order to investigate the next part a thorough review of the police reports was needed.
Working through the gaps
Since there are gaps in the chain in terms of device and perpetrator, focusing efforts on those two areas became an obvious route for the attorney to take. This began by reviewing the reports from the execution of the search warrant, where it was noted that there were six other males at the property at the time. Although a laptop and two cellphones had been collected there were photographs of six other cellphones on the property that did not appear to have been collected and/or analyzed.
Why is this important?
Since the device used to access Kik was not definitively found by law enforcement, if any of these males had logged into Kik or Yahoo using their own cellphones via Mr Defendants WiFi, the AT&T IP information provided to law enforcement would have been the same.
Challenging the two key chain paths
The Yahoo email was used to set up the Kik account and due to the IP being registered to a cell network company this tied directly to Mr Defendant. In challenging this it might be argued that someone close to Mr Defendant either used his email address to register the Kik account or used Mr Defendant’s login to Kik as their own.
The real trouble for the defense in this case was the still image of a male strongly resembling Mr Defendant wearing a dark hoody with white lettering matching an item of clothing he owned.
A final twist
In working through and focusing on these strands of the chain in isolation we were able to realize that there was an alternative explanation available for the still image in the Kik chat. Mr Defendant had a brother, similar in look, height and build, that was staying at the property at the time of the chat evidence. Whilst Mr Defendant had a dark blue hoody with white lettering, his brother had a near identical black hoody with the same lettering.
A review of the law enforcement reports revealed also that during the surveillance of the property they noted that the car belonging to the brother was using stolen license plates.
Conclusion
As you can see from these examples, the Chain of Suspicion can be very sneaky. A lot of the time, forensic reports will focus on the strong case. However, there will always be areas where you need to shine some light on, and if you do, you could find new evidence. Of course, there’s always the possibility that you won’t really find anything. But in the end, the thing that matters is to answer all the questions you have while pursuing any leads that arise.
The case mentioned above shows that if you just skim the data, it’s easy to say that Mr Defendant is obviously guilty. But once you delve into the other details and study the situation more, you can see that he could have been mistaken for his brother. Even if these exercises might be time-consuming, they could help build a defense.
As a forensic examiner, you always want to understand the case and study every single detail. You also need to show what is challengeable and not fully decided. Show everything from a different perspective, and that will help them through the discovery process.
Simon also explains this in a great video that you can view here.



